How AI Assistants are Moving the Security Goalposts

AI-based assistants or “agents” — autonomous programs that have access to the user’s computer, files, online services and can automate virtually any task — are growing in popularity with developers and IT workers. But as so many eyebrow-raising headlines over the past few weeks have shown, these powerful and assertive new tools are rapidly shifting […]
Who is the Kimwolf Botmaster “Dort”?
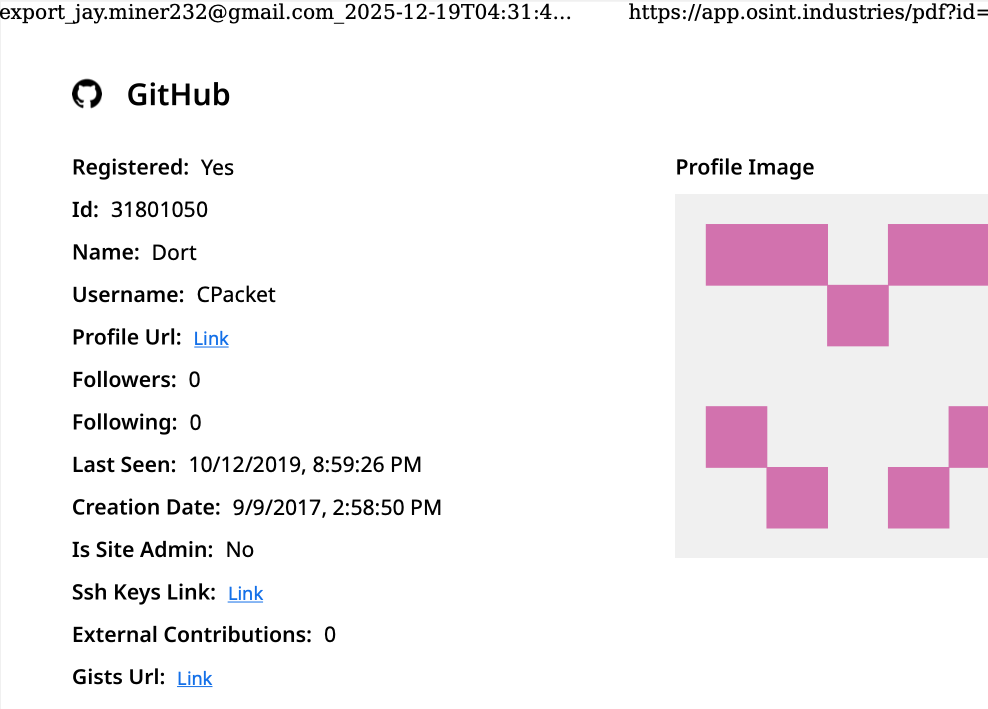
In early January 2026, KrebsOnSecurity revealed how a security researcher disclosed a vulnerability that was used to build Kimwolf, the world’s largest and most disruptive botnet. Since then, the person in control of Kimwolf — who goes by the handle “Dort” — has coordinated a barrage of distributed denial-of-service (DDoS), doxing and email flooding attacks […]
‘Starkiller’ Phishing Service Proxies Real Login Pages, MFA

Most phishing websites are little more than static copies of login pages for popular online destinations, and they are often quickly taken down by anti-abuse activists and security firms. But a stealthy new phishing-as-a-service offering lets customers sidestep both of these pitfalls: It uses cleverly disguised links to load the target brand’s real website, and […]
Kimwolf Botnet Swamps Anonymity Network I2P
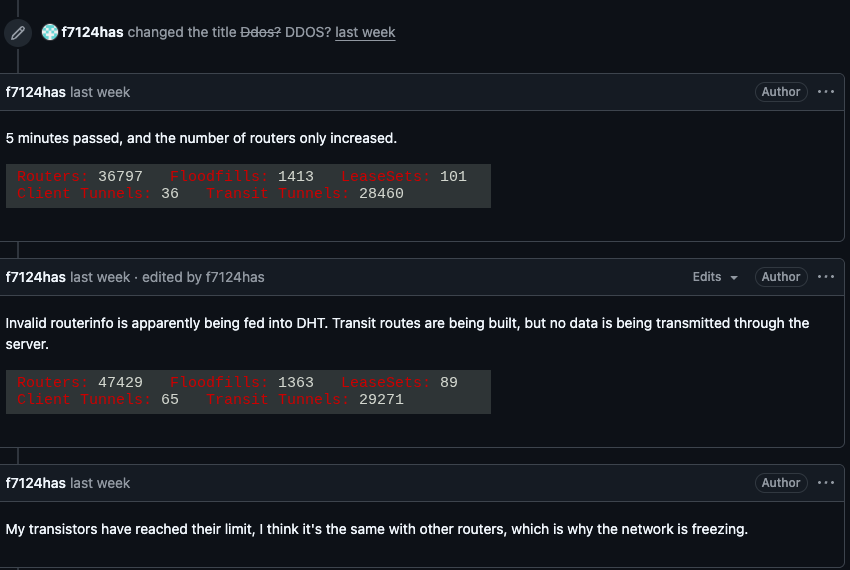
For the past week, the massive “Internet of Things” (IoT) botnet known as Kimwolf has been disrupting The Invisible Internet Project (I2P), a decentralized, encrypted communications network designed to anonymize and secure online communications. I2P users started reporting disruptions in the network around the same time the Kimwolf botmasters began relying on it to evade […]
Patch Tuesday, February 2026 Edition
Microsoft today released updates to fix more than 50 security holes in its Windows operating systems and other software, including patches for a whopping six “zero-day” vulnerabilities that attackers are already exploiting in the wild. Zero-day #1 this month is CVE-2026-21510, a security feature bypass vulnerability in Windows Shell wherein a single click on a […]
Navigating Cloud Compliance: Essential Regulations in the Digital Age
The mass migration to cloud-based environments continues as organizations realize the inherent benefits. Cloud solutions are the technology darlings of today’s digital landscape. They offer a perfect marriage of innovative technology and organizational needs. However, it also raises significant compliance concerns for organizations. Compliance involves a complex combination of legal and technical requirements. Organizations that […]
Leveraging Microsoft Forms for Data Collection & Surveys

Data has become the lifeblood of every organization, regardless of industry or sector. Today, a business’s ability to collect, analyze, and act on data is not just an advantage, it’s essential for survival. Data-driven decision-making enables organizations to respond quickly to market changes, identify new opportunities, and improve operational efficiency. When decisions are backed by […]
How to Use AI for Business Productivity While Staying Cyber-Secure

Most organizations have realized that AI is not a sentient system looking to take over the world, but rather an invaluable tool. They have come to utilize it to improve their productivity and efficiency. AI solutions have been installed at an astounding rate. Some are used to automate repetitive tasks and to provide enriched data […]
Your Business’s Digital Compass: Creating an IT Roadmap for Small Business Growth

Small businesses often struggle to leverage technology effectively. It can be a challenge just to survive, much less thrive. In many cases, they instinctively fall back on a reactive approach to IT challenges, rather than planning and acting proactively. That’s where an IT roadmap can help. It becomes a digital compass for organizations, a strategic […]
Cracking Down on Credential Theft: Advanced Protection for Your Business Logins

During an era of digital transformation, data and security are king. That is why, as cyber threats evolve in this age of digital transformation, businesses need to be prepared. Credential theft has become one of the most damaging cyber threats facing businesses today. Whether through well-crafted phishing scams or an all-out direct attack, cybercriminals are […]
